Investigating The Security and Digital Forensics of Video Games and Gaming Systems
A study of PC games and PS4 console
Funding provided by the College of Sciences Dean’s Office
Lei Chen and Narasimha Shashidhar
Department of Computer Science
Sam Houston State University
Huntsville, TX
Abstract—As video games received rapidly increasing attention, modern video games are often concerned with security and privacy issues. Many such video games and game console systems graciously allow player customization, giving people with malicious intent a new vector to lunch security attacks and exchange secretive messages, which posts new challenges to the society of security and digital forensics. In this research, we investigate the security of four popular PC video games and the Sony PlayStation 4 (PS4) game console. Our study showed that each of these video games has at least one feature that may possibly be exploited by attackers for transmitting secretive information, which is very difficult to be detected using current forensic tools. While the hard drive of PS4 console is encrypted and consequently most part of its file system cannot be analyzed using current forensic tools such as AccessData’s Forensic Toolkit (FTK), it is still possible to lunch Denial of Service (DoS) attacks and ARP cache poisoning, which may slow down and halt the system and potentially expose security sensitive information. Based on the above findings, we offer recommendations on how and where security professionals and digital investigators may search for hidden data.
Keywords—security, digital forensics, video games, game consoles, PS4, hidden information
INTRODUCTION
In software engineering, it is common sense that software complexity should be controlled at a low or manageable level whenever possible. The higher level of software complexity normally comes with higher risks of unintentional interference and interaction, and therefore potentially leads to more defects and security problems. This is also true in game software as well as gaming systems. As video games and gaming consoles offer players with more features and flexibility in this ever- growing industry, they also open up new vectors that may be exploited for malicious intent and activities.
Video games in the past had less complexity and allowed very little customization to the players. Without the internet, almost all video games in the old time only allowed four or few players to play simultaneously. With the growing of the internet as well as other new technologies and advancement of computer hardware, all popular video games and major gaming console systems give freedom to the players in selecting and customizing their game characters, gaming environments such as maps and levels, and exchanging messages both online and offline.
In the recent years, security professionals are facing new problems generated by hackers lunching attacks using video games or related channels, such as the PlayStation Network (PSN). Digital investigators also find challenges in identifying and acquiring evidence in game systems and files due to their proprietary formats and encapsulation nature. Modern video games are commonly categorized into several different genres, such as First Person Shooter (FPS), Massively Multiplayer Online Role Playing Game (MMORPG), Real Time Strategy (RTS), and Multiplayer Online Battle Arena (MOBA) [1][15]. While different genres of video games may have very different design and implementation of the game environment and characters, they all typically have a level of customization allowing players to transfer data (mostly text, pictures, and audios) and/or to (often intentionally) hide and display data. One such example is a common feature in MMORPGs and MOBAs that allows in-game add-ons. Such add-ons may help improve game playing experience by having customized visual and sound effects and user interface. The capability of the in- game add-ons is dependent to how much freedom the video game allows, e.g. what Application Program Interfaces (APIs) are provided and what kind of access privileges are given to add-on designers.
Security issues not only reside in video games, but also in the hardware and file systems, as well as the associated networks [16]. Several research studies showed their findings in the security problems found in game consoles such as the Sony PlayStation (PS) and proposed the best practice methodology for digital investigation on such systems. Our research in this study not only addresses the security problems of contemporary video games, but also the findings from our security testing and digital investigation on a PS4 console. We also give suggestions to investigators what to search and where in the file systems and consoles to search them.
Section II of this paper examines the security concerns and provides suggestions for digital forensic investigation in four popular video games. In Section III, we discuss our security testing and forensic analysis on one of the most popular game console systems, PS4. Section IV contains the conclusion of our research and lays out future futures. References are listed at the end of the paper.
VIDEO GAME SECURITY CONCERNS AND DIGITAL FORENSICS ANALYSIS
Our security examination and forensic analysis was conducted over four popular video games: World of Warcraft (WoW), League of Legends (LoL), Defense of the Ancients 2 (DotA 2), and StarCraft 2 (SC2). These games are chosen for the reason of their popularity and high level of player customizable features. In this section, we briefly introduce each of these games and discussed our findings.
World of Warcraft
WoW was released in 2004 and has been very popular around the world with more than 10 million players [2]. While in the earlier version of game launcher a player logs in before redirected to launcher for game updates, the recent version enforces a pre-login launcher indicating that hacking to the game may require bypassing the player login authentication. WoW allows high level of game customization by permitting players’ add-ons. Such add-ons may tailor players’ game experience by customizing things like user interface and warning notifications [3]. Almost all WoW add-ons are programmed using Lua and XML, and anyone familiar with these programming languages can create add-ons and publish them on game community forums for others to download [4].
There two types of exploits in WoW: add-ons and game file modification. While game file modifications require more advanced understanding of game programming and compilation, add-ons are relatively simple – anyone who can write code in Lua and have the add-on pass the basic requirement can share it with others. Mainly due to this reason, it is often very difficult to identify a malicious add-on from the benign. For digital forensic investigators, it is extremely difficult to acquire evidence if it resides in the exchanged data between players using such add-ons because current forensic tools are not capable of detecting or pulling such data that is encapsulated in game or add-on files. Two such example add- ons we found in WoW are Augmented Virtual Reality (AVR) and Augmented Virtual Reality Encounters (AVRE) [9][10], both of which allow players to draw and place textures on top of game. Modifying game files is also possible by using a .MPQ editor, Ladik’s MPQ Editor as an example. .MPQ files are large archive files used by Blizzard to store archive files [7][11][12]. It allows feature like swapping a human photo with the game characters. A modified WoW.exe is also required to remove certain check values to allow such game modification. For digital investigation practice, we suggest to hash the .MPQ files on target machine and compare them to originally released .MPQ hashes for identifying potential evidence.
League of Legends (LoL)
LoL, a MOBA genre video game, was released in late 2009 and immediately received wide welcome around the world. In just 3 years, the number of registered players climbed to over 70 million, of which more than 32 million players were active with at least one log-in each month [5]. One of the reasons of the rapid growth of player community is that LoL is free of cost. LoL enforces user authentication immediately after game update every time when the game is launched. The game spectator system allows other players logged into the game to watch live matches [5]. While these features combined win a huge number of players, they also created potential channels that may be used by attackers.
In LoL, an attacker may possibly modify using custom UI mods, the elements of game launcher and the login screen [8][13]. LoL’s launcher runs from a .SWF file (Shockwave Flash) with name “RADS”. An attacker can not only change elements like the background picture and associated hyperlinks
of the splash menu, but also add other arbitrary content, as long as the patching and verification components of the launcher are not modified. The login screen supports moving background (login.SWF), static background (.PNG), and associated audio (LoginScreenLoop.MP3). These files potentially serve as channels for exchanges of secret information. By comparing the hashes of the official launcher and/or login screen game files with those on the target machine, an investigator can identify which, if any, of the game files have been altered. From there, it is up to the investigator to uncover any message or link that was imbedded into these files using tools appropriate for the different file types.
Defense of the Ancients 2 (DotA 2)
DotA 2 and LoL are similar in terms of genre, but different in several ways: aesthetics, the spectator system, and the launcher [6]. DotA 2 launches from the widely used Steam client, a content distribution platform for many games. Consequently, player customization comes through the Steam Workshop, where players can create items for their game characters and upload team banners and logos [6]. Such player created items are submitted to and approved by the community before added to the actual game. The DotA 2 spectator tools allow a spectator to write on the game screen.
DotA 2 gives much freedom to players to design and integrated the design into the actual game. For example, players can create messages using 3D modeling techniques and have them displayed in game environment [6]. As long as pictures follow the appropriate format (pixel size, .PNG file, and no vulgarity), any content (including photos with hidden message embedded using steganography) can be used.
Perhaps the biggest issue regarding DotA 2 involves the spectator tools. Since DotA 2 was built from the core with E-Sports in mind, the developers wanted to make DotA 2 to have revolutionary features that E-Sports casters and commentators could take advantage of. In ordinary use, these tools help the E-Sports caster communicate the progression of a match and the battles within to the audience. However, an attacker can exploit these tools along the same lines as one could have with AVR in WoW. The feature in question is the freehand drawing tool. DotA 2 spectators have access to this tool with the intention of it being used similar to how sports commentators might outline a play in a game such as football. Any drawings made by the spectator can be seen by any other spectator watching that game and the drawings last for less than a minute. However, the drawings are not recorded in the game replays, so unless DotA 2 is storing this relatively useless spectator data privately, there is no way for the actions to be recovered. Thus, an attacker could draw in a section of the map where people would not normally be looking and communicate a message to the accomplice spectator in that game.
With the previous games that modified existing game files, we could compare the hashes of the official game files against those on the target machine. Since the custom items are user generated content, there is no baseline or signature that can be used to flag an item for suspiciousness. The only saving grace is that for an item to be officially accepted into the game, it must be approved by the game developers. Therefore, this method may not be feasible for an attacker who wants to transmit a message quickly. On the other hand, the team pictures are much easier to upload to the game. Therefore, an attacker would be much more inclined to send the message through the pictures since there is no waiting period. Fortunately for the investigator, the pictures can be pulled and processed like any standard .PNG file. The only method that presents no recourse for investigators involves the freehand drawing tool.
StarCraft 2 (SC 2)
StarCraft series has been one of the most successful products by Blizzard. Both StarCraft 1 and 2 allow players design their own battle maps and make them available on Battle.net to all players. The map editor Galaxy allows extensive modification such as interface overhauls, triggers, alert messages, and even cinematics. This potentially creates security concerns.
The main idea in hiding information in StarCraft 2 is that the attacker can use the Galaxy Editor to create a map and upload it to the Arcade on Battle.net. Inside the map, he or she might, for example, add an event or trigger that will display the secret message when the trigger is activated. Due to the sheer power of the Galaxy Editor, triggers can easily become much more complex. This means that the trigger itself can be nested far below legitimate ones. With the Galaxy Editor, the limitations on how intricate and nuanced the map rely solely on how much the map creator puts into his or her creation.
StarCraft 2 comes with a few conveniences that investigators can make use of. The first is that Battle.net keeps track of recently played maps. So, if the attackers are only using SC2 to transfer messages through the same map, an investigator could note what the only recently played map is and recommend an investigation of the map. Once the target map has been determined, the investigator can attempt to locate it on suspect machines. The map creator will typically have his or her own copy of the map which should have a .SC2MAP file extension that can be opened with the Galaxy Editor. If the target map cannot be found, it must be pulled from Battle.net. Once the map has been downloaded, it should appear in the Battle.net cache associated with SC2's game installation folder. The target file will have a .SC2MA file extension. The file size will vary based on the map data within the file, but the target .SC2MA file is usually one of the larger ones. Copy the .SC2MA and run it through a .SC2MA/.SC2MAP converter such as the one by the Modbox group to ensure that all settings and data are carried over [14]. Once the .SC2MAP file is acquired, it becomes a task of searching through the triggers one by one in search of anything suspicious. Additionally, an investigator may need to visually look at the map in order to detect messages written using the editor's texture brushes.
PS4 SECURITY TESTING AND DIGITAL FORENSICS ANALYSIS
Among the video gaming consoles available in the market, Play Station (PS) consoles fall in our interest. While there are reports of PS3 attacks and researchers have performed forensic analysis on these systems [17][18][19][20], PS4 has received very few reports on its security issues and forensic analysis. To our best knowledge, the most recent reliable report was that Davies et al. performed forensic analysis and testing on a PS4 console and published findings and proposed their best practice methodology for PS4 forensic investigation in March 2015 [16]. In their analysis and testing, their interests fell on features such as the PlayStation Network (PSN), Sony Entertainment Network (SEN), Internet Browser, ShareFactory, System Storage Management, Error History, What’s New, Trophies, Profile, Friends, Party Messages, and Messages. Partially based on their research, our team conducted security test and forensic analysis in the summer of 2015. Below are the findings (including some verifications of previous findings) from our research.
Our research team conducted testing by launching two security attacks to the PS4 console, an ARP (Address Resolution Protocol) poisoning packet hijacking attack and a denial of service (DoS) attack.
For the memory overflow attack, we connected our PS4 and a Windows PC on the same LAN subnet. Cain & Abel version
4.9.56 was installed and launched on the Windows PC. Disregarding the warning from Windows Firewall on the PC, Cain & Abel scanned the MAC addresses on the network and found the corresponding IP address of the PS4. The ARP poisoning attack was launched and data packets associated with our PS4 were hijacked.
The t50 tool on 64-bit version of Kali was used for our DoS attack testing. On Kali, the command “t50 –flood 192.168.1.2” started flooding the PS4 on the IP address. The flood caused PS4 data traffic to slow down and halt at the end. The PS4 did not recover until the flood was manually stopped. The PS4 sometimes even had to be restarted to return to its normal functioning status.
The above security testing indicated that PS4, just like a computer, is subject to common network attacks.
Forensic Analysis
It is confirmed in our research that the 500GB PS4 hard drive we used was encrypted. Our team made in image of the encrypted PS4 hard drive and copied it to an external 750GB (reformatted to NTSF) hard drive. While the most recent FTK Imager (version 3.4.0) was capable of producing the image, the encrypted image provided no insight to our investigation. Therefore, we conclude that the most useful information must come from the game console’s user interface. The PS4 hard drive had an unknown file system with 15 partitions (Figure 1) on our 500GB hard drive. Our team has discovered that the PlayStation 4 Operating System is base on FreeBSD 9.0 and a list of the 50 open source software used in PS4 OS can be found on this website http://www.scei.co.jp/ps4-license/
In an effort of attempting to save application data in attached an external USB flash drive, we noticed that our 8GB USB Sandisk flash drive with NTFS file system was not accepted by PS4. But reformatting it with FAT32 (exFat was also tested to be acceptable) allows PS4 to accept it. Saving application data to external USB flash drive in our case generated a main folder “PS4” in the flash drive with sub-folder “SAVEDATA”, inside which we found a couple of sub-folders with scrambled names. In each of these sub-folders, there are a few folders with naming scheme of “CUSA” followed by 5 digits (Figure 2). When one of these “CUSA” folders was opened, two different files with the same name can be found, with one having unrecognized file type and the other being a .bin file (Figure 3). In the .bin file, we found the content starts with “pfsSKKey” followed by unreadable characters. While we are not able to confirm from other sources, we suspect that “pfsSKKey” may indicate that the unreadable characters are actually PlayStation File System Shared Key in a scrambled format. We also discovered that our FIFA 2015 screen shots taken during gameplay were saved in the PS4>SHARE>Screenshots>FIFA 15 sub-folder. While PS4 allows saving screenshots to external USB drives, it does not allow transferring screenshots in the opposite direction to PS4.
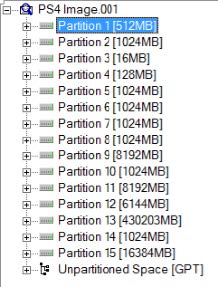
Figure 1: PS4 hard drive image with 15 partitions
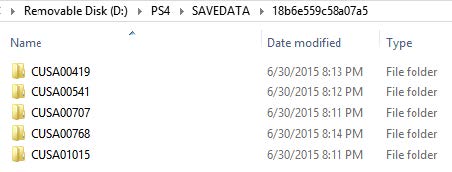
Figure 2: Directories and files created by PS4 in a USB flash drive in an attempt to save application data
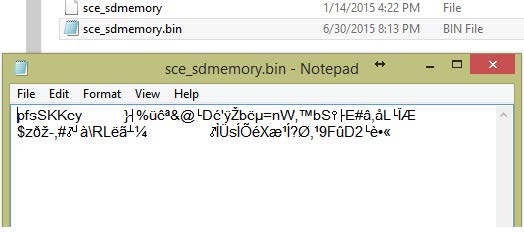
Figure 3: File created by PS4 in USB flash drive potentially contains the Playstation File system Shared Key
CONCLUSION AND FUTURE RESEARCH
As demonstrated, there are many exploitable vectors that may potentially be used by attackers as the level of player driven customization rises. The field of video game forensics is still in an infantile stage, and may risk being perpetually in that stage given how fast the industry grows and how video games rapidly change. However, the key idea behind all of our research is that most vulnerabilities lie within the user generated content and programming interfaces accessible by users and players. Since user generated content capability is such a powerful draw to players, game companies are incredibly likely to continue to provide support for such content. Therefore, even more and new attack vectors will open. As a result of our study, however, we conclude that if there is a chance of video games being exploited, the first areas to check are those that are popular in the modding communities associated with the games. Additionally, we learned that the games similar to SC2 Arcade and GMod maps tend to give more freedom to potential attacks making use of player customizations. An investigation into these will require thoroughly examining the specific map resources and, even then, there is no guarantee that the suspicious data will be recognizable without seeing its visual representation.
To stress one other point, we also want to remind the gravity generated by E-Sports. A game with a large E-Sports calling will likely become a very popular game as well as have tools such as the DotA 2 spectator (caster and commentator) tools. These tools could also be exploited, but, more importantly, the popularity of a game should not deter an investigator to forensically searching through the game. We urge that just because a game is popular and on virtually every machine, it should not be automatically ruled out.
As aforementioned, the future of video game forensics will only grow, especially if the trend of support for user generated content continues. Hopefully as the field grows, video game forensics tools will begin to appear as well as supporting modules for existing forensics tools. There is also room for tools that parse data from entities such as the Galaxy Editor's trigger list as well as tools that can offer visualizations of data for situations with brush textures in GMod. With advances in forensics like these, investigators can even the playing field against attackers with the motivation of hiding information in video games.
As for video gaming console systems, while manufactures are making their effort in protecting the hardware, gaming operating systems, gaming file systems, as well as play data and application data, it is inevitable that attackers will find (new) vectors to hack into the systems. Encrypting the hard drive on one hand helps secure the system and data, but on the other hand creates a huge obstacle in digital forensic investigations as none of the existing tools is capable of exploring the encrypted content and cracking such encryption is just impractical. In such cases, it may be required to acquire the encryption key from the suspect or an unencrypted copy of the content to be acquired.
